OT Security
26.May.2025
Building a More Resilient OT Security Framework with IEC 62443‑3‑2 & 3‑3
Industrial control (OT, Operational Technology) environments often feature aging equipment running continuously, unable to update as frequently as IT systems, leading to cybersecurity gaps. When OT systems are compromised, the impact extends beyond operations—it may threaten human safety. Recent cyber incidents targeting critical infrastructure sectors like manufacturing, energy, and transportation highlight that OT security must be a top priority.
Norris Chen, Senior Engineer at DEKRA Onward Security’s Cybersecurity Assessment Division, explains that the IEC 62443-3-2 and 3-3 standards are essential frameworks for securing critical infrastructure, including manufacturing, energy, and transportation. By applying systematic risk assessment and security controls, organizations can build a more resilient OT security perimeter.
Norris elaborates that IEC 62443 takes a holistic, risk-based approach to cybersecurity in OT. Rather than a single standard, it’s a comprehensive framework comprised of key modules:
These modules help organizations implement security across three dimensions: governance, systems, and product development. Whether you’re a manager, system architect, or device developer, this framework provides the tools and rationales needed to enforce robust cybersecurity.
Integrating IT and OT security, IEC 62443 offers a consistent methodology that helps Taiwanese industries bolster critical infrastructure resilience and align with international compliance standards.
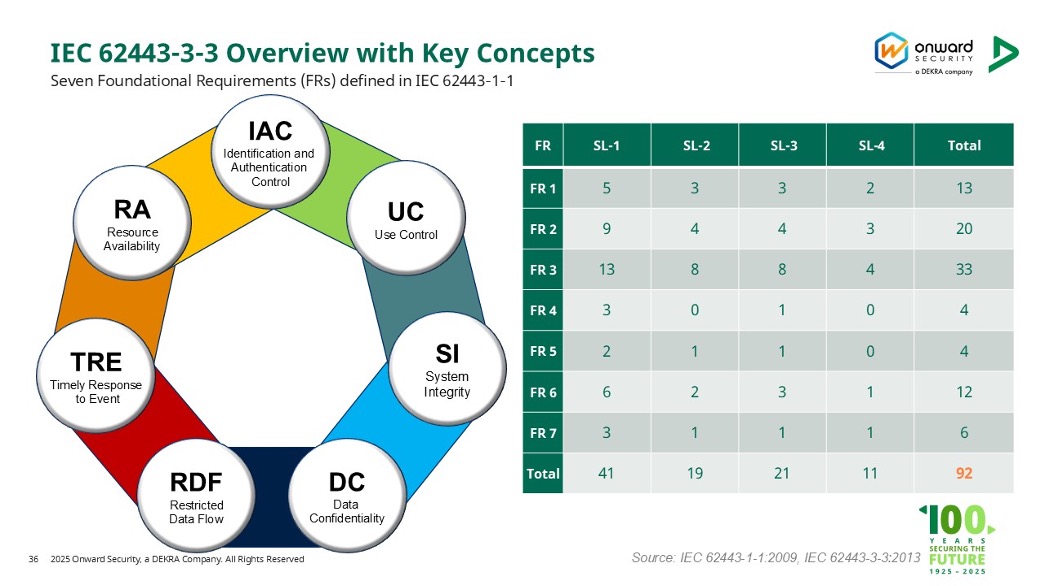 IEC 62443-3-3 defines seven foundational requirements (FRs) to ensure core cybersecurity for industrial control systems:
IEC 62443-3-3 defines seven foundational requirements (FRs) to ensure core cybersecurity for industrial control systems:
IEC 62443 assesses cybersecurity readiness via two complementary axes:
Practical Considerations for OT Security Implementation:

Norris Chen, Senior Engineer at DEKRA Onward Security’s Cybersecurity Assessment Division, explains that the IEC 62443-3-2 and 3-3 standards are essential frameworks for securing critical infrastructure, including manufacturing, energy, and transportation. By applying systematic risk assessment and security controls, organizations can build a more resilient OT security perimeter.
Norris elaborates that IEC 62443 takes a holistic, risk-based approach to cybersecurity in OT. Rather than a single standard, it’s a comprehensive framework comprised of key modules:
- 2-1: Security Management System (SMS)
- 3-2: Risk Assessment & Security Design Methods
- 3-3: System-Level Security Requirements
- 4-1: Secure Software Development Lifecycle (SSDLC)
- 4-2: Component-Level Security Requirements
These modules help organizations implement security across three dimensions: governance, systems, and product development. Whether you’re a manager, system architect, or device developer, this framework provides the tools and rationales needed to enforce robust cybersecurity.
Integrating IT and OT security, IEC 62443 offers a consistent methodology that helps Taiwanese industries bolster critical infrastructure resilience and align with international compliance standards.
IEC 62443‑3‑3: Seven Foundational Security Requirements for OT Systems

- IAC – Identification & Authentication Control: Ensure users are correctly identified and authenticated.
- UC – Use Control: Manage user access to system functions.
- SI – System Integrity: Prevent unauthorized modification of data/systems.
- DC – Data Confidentiality: Protect sensitive information from unauthorized access.
- RDF – Restrict Data Flow: Control network communication paths to prevent unauthorized data transfer.
- TRE – Timely Response to Events: Enable quick detection and handling of security incidents.
- RA – Resource Availability: Ensure critical systems remain operational and protected from service disruption.
Dual Evaluation of OT Security Capabilities
IEC 62443 assesses cybersecurity readiness via two complementary axes:
- Security Level (SL) (per 3-3 & 4-2): evaluates the technical ability to withstand threats.
- Maturity Level (ML) (per 4-1 & 2-4): evaluates the maturity of supplier or integrator security processes.
Practical Considerations for OT Security Implementation:
- Role of External Components
OT security depends not only on the control system itself but also on integrated components such as centralized authentication servers, SIEM systems, firewalls, and network monitoring tools. These external elements reinforce the core system and enhance overall protection. - Balancing Security Level and Operability
As Norris notes: “A higher security level isn’t always better.” In high-availability environments, overly strict controls, such as multi-factor authentication for high IAC levels, could prevent operators from accessing systems during emergencies, creating operational risks. The framework encourages compensating controls (e.g., enhanced physical security, thorough personnel background checks, and dual-operator requirements) when strict security could hinder essential operations.
Continuous Improvement Over One-Time Compliance
Norris emphasizes that cybersecurity threats are constantly evolving, and IEC 62443 should be viewed as a continuous improvement framework, not just a checkbox for compliance. Security designs must balance risk versus practicality, align with real business needs and environmental contexts, and avoid blind pursuit of the highest security level. Only through periodic risk assessments and control updates can organizations maintain OT system resilience in dynamic threat landscapes.






